PUF-based Authentication
Utilizing Physical Unclonable Functions (PUFs) to create a robust challenge-response mechanism for vehicle authentication.
Overview
Traditional cryptographic methods are becoming insufficient because they are vulnerable to sophisticated side-channel attacks, cloning attempts, and tampering threats. Physical Unclonable Functions (PUFs) offer a promising solution due to their inherent uniqueness and resistance to cloning.
Our research focuses on integrating PUFs into a comprehensive challenge-response mechanism that ensures the security and efficiency required for Autonomous Vehicles (AVs). By utilizing the unique physical characteristics of hardware devices, we can create authentication systems that are extremely difficult to clone or tamper with.
Research Problem
- Vulnerability of traditional cryptographic methods to side-channel attacks
- Risk of key extraction and cloning in software-based security
- Need for hardware-based security solutions that are resistant to physical tampering
- Challenges in implementing PUF-based authentication in resource-constrained environments
- Lack of robust frameworks for real-world adversarial testing of PUF solutions
Research Objectives
- Develop a PUF-based challenge-response mechanism for robust vehicle authentication
- Research current PUF technologies and their use cases in security systems
- Analyze the benefits of different PUF types for vehicle authentication
- Develop a challenge-response mechanism utilizing PUF technology
- Conduct rigorous testing under various environmental scenarios
Methodology
Our approach utilizes Field-Programmable Gate Arrays (FPGAs) to implement PUF-based authentication with a robust challenge-response mechanism.
System Architecture
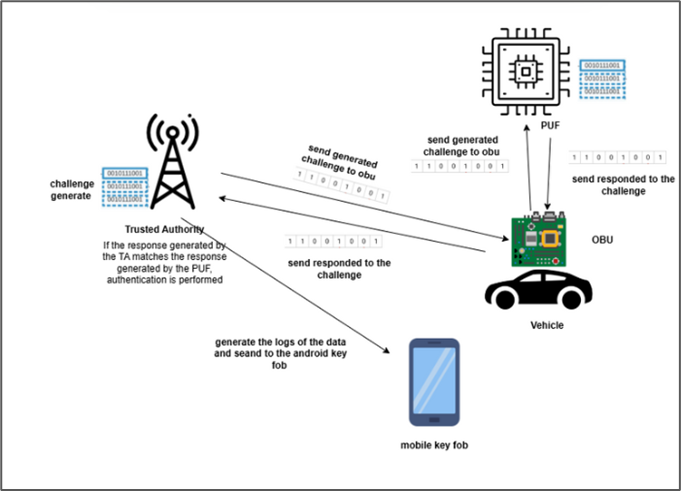
The PUF-based authentication system consists of three main components:
- Challenge Generation: A secure random number generator creates unpredictable challenges.
- PUF Implementation: FPGA-based PUF that generates unique responses based on physical characteristics.
- Verification System: Database and comparison mechanism to authenticate responses.
PUF Implementation
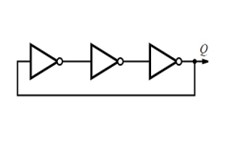
- Ring Oscillator PUF
- FPGA hardware
- HDL programming
- 32 Ring Oscillators
- 8-bit counters
Challenge-Response
- 128-bit challenges
- CSPRNG for generation
- UART communication
- Hamming distance verification
- Response logging
Verification System
- Python Flask server
- Database storage of CRPs
- Real-time verification
- Mobile app integration
- Audit logging
Current Progress
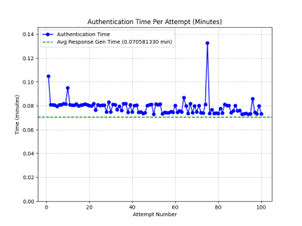
Our research has made significant progress in implementing and testing the PUF-based authentication system:
Challenge Generation & Transmission
We have successfully implemented the challenge generation module and established transmission via a Python Flask server.
FPGA Implementation
We have programmed the FPGA using HDL to generate responses and implemented a UART-USB interface for challenge transmission and response reception.
FPGA Hardware

Ring Oscillator Implementation
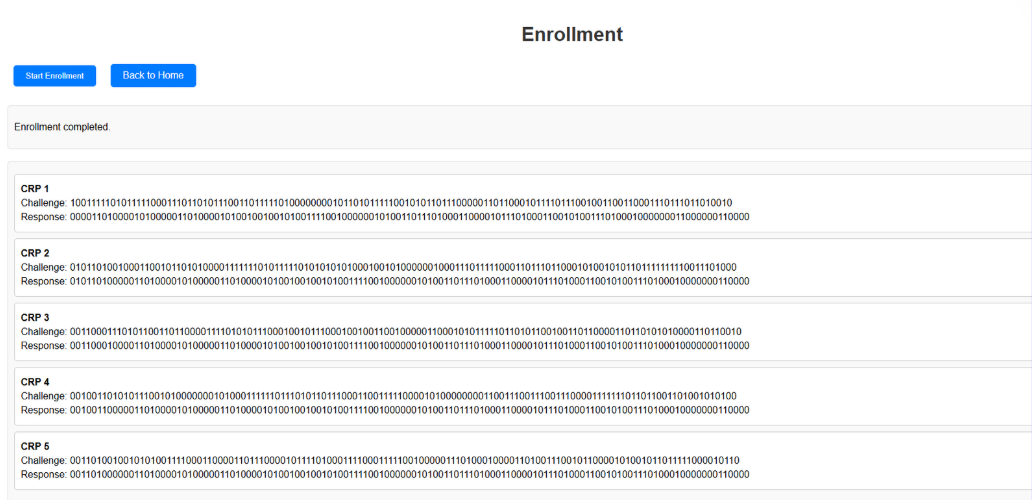
Database Integration & Authentication Process
We have stored generated challenges and responses in a database and implemented the verification process where the server selects a stored challenge, exchanges it with the PUF, and compares the generated response with the stored response.