Secure V2V/V2I Communications
Implementing lightweight ECC for secure Vehicle-to-Vehicle and Vehicle-to-Infrastructure communications.
Overview
Current authentication mechanisms for Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) communications primarily use traditional cryptographic methods, which are becoming increasingly vulnerable to sophisticated attacks. Black hole attacks, where malicious nodes drop packets, pose a significant threat to network reliability and safety in vehicular networks.
Elliptic Curve Cryptography (ECC) offers stronger security with smaller key sizes, making it suitable for resource-constrained environments like vehicular networks. Our research focuses on implementing a lightweight ECC-based authentication mechanism to secure V2V and V2I communications while mitigating black hole attacks.
Research Problem
- Vulnerability of V2V/V2I communications to black hole attacks
- Limitations of traditional cryptographic methods
- Resource constraints in vehicular networks
- Need for lightweight yet secure authentication mechanisms
- Lack of trust-based security frameworks for vehicular networks
Research Objectives
- Design and implement a lightweight authentication mechanism using ECC for V2V communication
- Mitigate blackhole attacks in vehicular networks through secure authentication
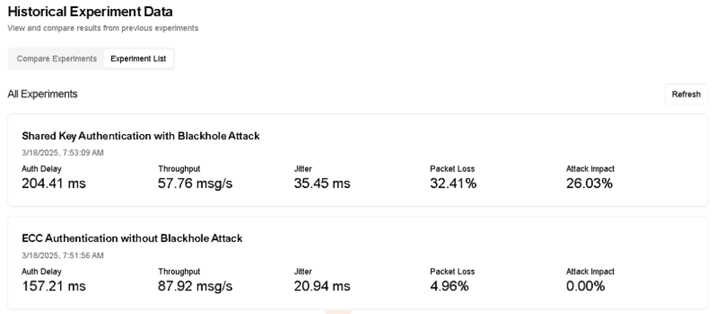
- Evaluate performance metrics including authentication delay, throughput, jitter, and packet loss
- Quantify the impact of blackhole attacks on network performance
- Add trust level security among vehicle nodes and blacklist attacking vehicles
Methodology
Our approach combines hardware implementation, cryptographic techniques, and performance evaluation to create a secure and efficient authentication mechanism for vehicular networks.
System Architecture
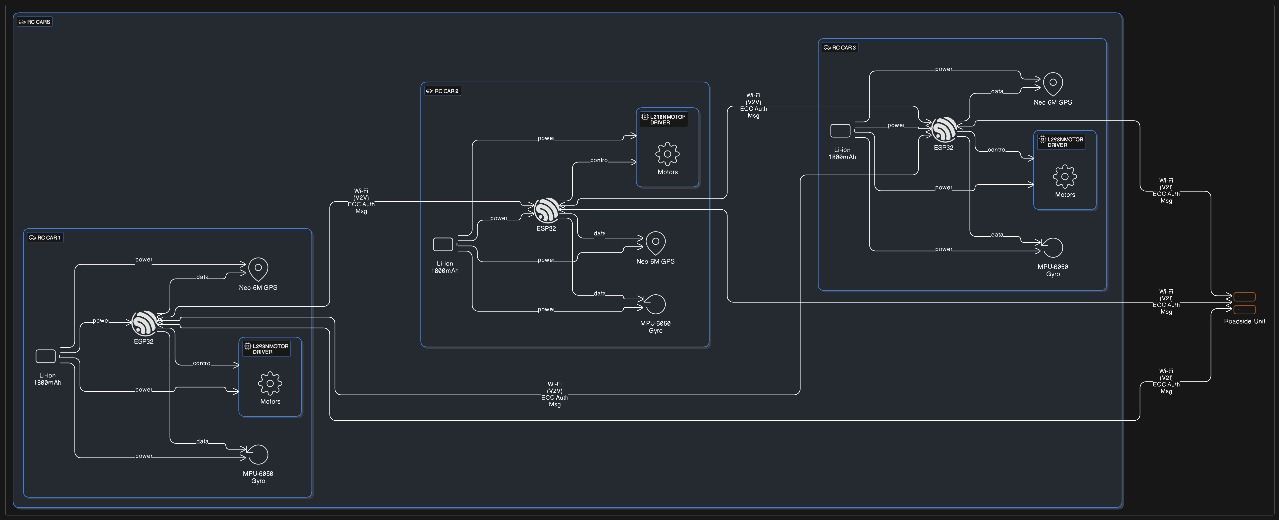
The system architecture consists of three main components:
- Vehicle Nodes: ESP32-based devices with sensors that simulate vehicles in the network.
- Authentication Mechanism: ECC-based authentication protocol implemented on the ESP32 devices.
- Monitoring System: WebSocket server that collects and analyzes performance metrics.
Hardware Setup
- ESP32-WROOM 32
- MPU-6050 sensors
- GPS modules
- SD card modules
- Voltage stepdown modules
Authentication
- ECC Curve25519/secp256r1
- Secure key storage
- Optimized cryptographic operations
- Trust-based mechanism
- Blacklist for malicious nodes
Performance Metrics
- Authentication delay
- Maximum authentication time
- Minimum authentication time
- Throughput
- Jitter and packet loss
Current Progress
Our research has made significant progress in implementing and testing the ECC-based authentication mechanism:
Hardware Implementation
We have successfully created three simulated vehicles using ESP32 devices equipped with sensors to mimic real-world vehicular networks.
Vehicle Nodes

Sensor Dashboard
Authentication Results
We have implemented and tested the ECC-based authentication mechanism, measuring various performance metrics to evaluate its efficiency and security.